Unlocking ISO 27001 Security Controls for Compliance

Elevating Information Security with ISO 27001: A Comprehensive Guide
Unlock the secrets to ISO 27001 security controls: mastering Annex A measures is your key to robust information protection and effortless compliance. Many organisations find it a challenge to translate ISO 27001 requirements into practical safeguards, leaving them vulnerable to data breaches and hefty regulatory fines. This comprehensive guide will show you how a structured set of 93 controls forms the bedrock of an effective Information Security Management System (ISMS). We’ll map out Annex A’s four core categories, delve into the significant 2022 update, and provide a step-by-step implementation plan—from initial gap analysis right through to continuous improvement. Discover how AI can streamline your evidence collection, explore the advantages and hurdles for SMEs, navigate the UK and European audit landscape, and access essential resources to help you request a quote or book an audit through our ISO 27001 certification services.
What Exactly Is ISO 27001 and Why Are Its Security Controls So Crucial?
ISO 27001 is the definitive international standard that outlines the requirements for establishing, implementing, maintaining, and continually enhancing an Information Security Management System. The Annex A security controls are the very foundation of your risk treatment strategy, specifying the measures needed to protect the confidentiality, integrity, and availability of your information. By adopting these controls, you effectively close gaps in your cyber defences and clearly demonstrate your commitment to compliance to all stakeholders. They are the essential building blocks of any high-performing ISMS, guiding your organisation through structured risk mitigation.
A Snapshot of the ISO 27001 Standard
ISO 27001 is a globally recognised benchmark that provides a robust framework for establishing, implementing, maintaining, and continuously improving an Information Security Management System (ISMS). Crucially, Annex A of the standard details a comprehensive suite of security controls designed to safeguard the confidentiality, integrity, and availability of your organisation’s information assets, forming the core of your risk treatment approach.
International Organization for Standardization, ISO/IEC 27001:2022 – Information security, cybersecurity and privacy protection — Information security management systems — Requirements (2022)
This authoritative citation underpins our discussion on the significance of ISO 27001 and its vital security controls.
What Does the Latest ISO 27001:2022 Standard Encompass?
The ISO/IEC 27001:2022 update reinforces core management system principles and refines Annex A, consolidating controls into 93 measures across four key themes. It features updated clauses covering organisational context, leadership engagement, strategic planning, essential support functions, operational execution, performance evaluation, and ongoing improvement. This latest version aligns seamlessly with other ISO management system standards, adopting a harmonised structure to enhance integration and audit efficiency.
How Does an Information Security Management System (ISMS) Function?
An ISMS is a systematic, structured framework designed to identify, assess, and manage information security risks through clearly defined policies, procedures, and controls. It operates on the proven Plan–Do–Check–Act (PDCA) cycle, ensuring that risk treatment remains dynamic and responsive. By embedding security practices into the fabric of your daily operations, an ISMS guarantees that your controls stay relevant and effective against evolving threats and your organisation’s strategic objectives.
Why Are Security Controls Absolutely Critical for Achieving Compliance?
Security controls are paramount because they translate high-level organisational policies into tangible, actionable steps that directly address specific threats. They empower your organisation to demonstrate due diligence to regulatory bodies and clients alike, significantly reducing the likelihood and impact of security incidents. Furthermore, well-implemented controls cultivate a strong security-aware culture, ensuring that compliance is not just a one-off achievement but a sustained commitment.
What Are the 93 Essential ISO 27001 Annex A Security Controls?
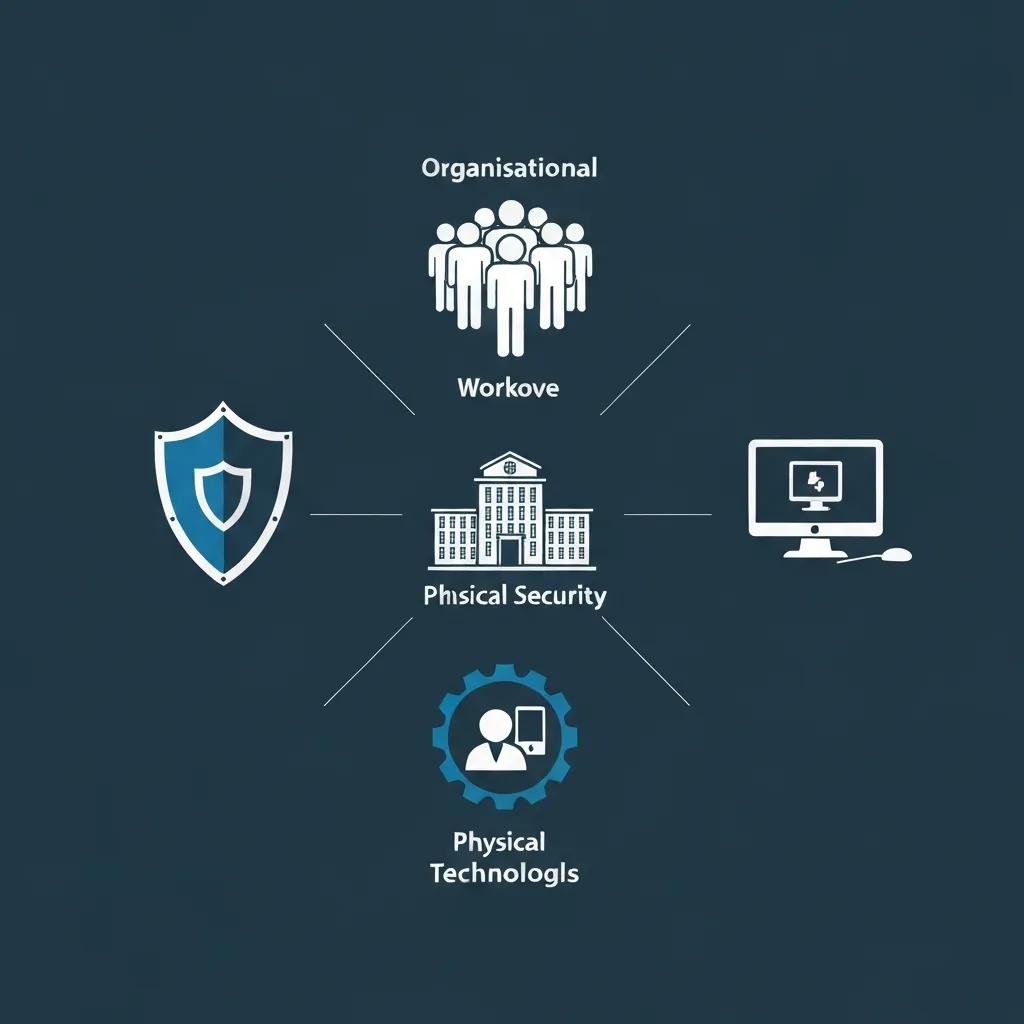
Annex A thoughtfully categorises 93 distinct controls into four core domains, each addressing specific facets of information security. This structured approach ensures comprehensive coverage, from overarching governance and management practices to the critical aspects of physical security and advanced technological safeguards.
A Closer Look at Annex A Security Controls
Annex A of ISO 27001 presents a comprehensive catalogue of security controls, meticulously organised into four key domains: Organisational, People, Physical, and Technological. These controls are indispensable for effectively mitigating information security risks and ensuring adherence to the standard. The significant 2022 update has realigned these controls to emphasise desired outcomes rather than rigidly prescriptive measures, encouraging organisations to tailor their application to their unique operational context.
ISO/IEC 27001:2022 – Information security, cybersecurity and privacy protection — Information security management systems — Requirements (2022)
This citation serves as a foundational reference for our explanation of the structure and strategic purpose of the Annex A security controls.
How Are the Controls Organised: Organisational, People, Physical, and Technological?
| Control Area | Key Focus | Primary Objective |
|---|---|---|
| Organisational | Governance and strategic management | Establishing clear roles, robust policies, and effective risk treatment strategies |
| People | Workforce engagement and security awareness | Ensuring staff competence, promoting security consciousness, and managing responsibilities |
| Physical | Facilities and equipment security | Preventing unauthorised access to premises, assets, and sensitive areas |
| Technological | Information systems and network security | Protecting digital assets through advanced technical safeguards and secure configurations |
Each domain tackles distinct security risks, and together they forge a formidable defence strategy. This categorisation naturally leads us to compare the previous controls with the updated 2022 revisions.
What Are the Main Distinctions Between the 2013 and 2022 Controls?
The ISO 27001:2022 update strategically realigns controls to focus on achieving specific outcomes rather than dictating rigid, prescriptive actions. Several controls have been consolidated or reclassified, and the terminology used for risk treatment has been simplified to promote greater flexibility. The revised Annex A encourages organisations to adapt controls to their specific circumstances, fostering a culture of pragmatic security rather than mere compliance through a checklist approach.
Which New Controls Have Been Introduced in ISO 27001:2022?
- Cloud Security – Establishes controls for the governance of cloud services and clear asset ownership.
- Threat Intelligence – Implements mechanisms for actively monitoring and responding to emerging threat feeds.
- Data Masking – Introduces techniques for obscuring sensitive information, particularly in non-production environments.
- Configuration Management – Defines policies for maintaining secure baseline configurations and managing changes effectively.
These crucial additions reflect contemporary best practices and significantly enhance resilience against sophisticated cyber threats.
How Do You Effectively Implement ISO 27001 Annex A Controls for Seamless Compliance?
Implementing the Annex A controls demands a systematic and well-thought-out approach, beginning with a thorough understanding of your organisation’s unique risk landscape and culminating in a cycle of continuous improvement.
What is the Essential Role of Gap Analysis and Risk Assessment?
A gap analysis is crucial for identifying any missing controls or discrepancies between your current security practices and the stringent requirements of ISO 27001. Following this, a comprehensive risk assessment prioritises potential threats based on their likelihood and potential impact, which then guides the selection of appropriate controls. Together, these processes establish a clear, actionable roadmap for your mitigation efforts and the strategic allocation of resources.
How Can You Develop a Highly Effective Statement of Applicability (SoA)?
Your Statement of Applicability (SoA) is a vital document that lists all Annex A controls, clearly indicates which ones are relevant to your organisation, and provides robust justifications for any inclusions or exclusions. It serves as a critical reference point for both internal and external audits, as well as for overall governance, directly linking your chosen controls to your assessed risks. Crafting a clear and concise SoA ensures transparency and powerfully demonstrates management’s commitment to information security.
What Key Policies and Procedures Are Essential for Supporting Control Implementation?
Policies establish the high-level strategic direction, while procedures provide the detailed, step-by-step instructions for execution. Essential supporting documents include:
- The overarching Information Security Policy, which sets the strategic objectives for your ISMS.
- An Access Control Procedure, detailing user provisioning, de-provisioning, and regular access reviews.
- An Incident Management Policy, outlining the process for reporting, responding to, and resolving security events.
- A Change Management Procedure, ensuring that all system updates and modifications are implemented securely.
Well-documented governance frameworks are fundamental to ensuring consistency and accountability across all implemented controls.
How Does a Commitment to Continuous Improvement Sustain Compliance?
Sustained compliance hinges on a robust continuous improvement strategy, driven by the Plan–Do–Check–Act (PDCA) cycle. Regular internal audits, thorough management reviews, and the consistent monitoring of performance metrics are key drivers for ongoing enhancements. This dynamic feedback loop ensures that your security controls remain agile and effectively adapt to new vulnerabilities and evolving business requirements, thereby preserving long-term compliance.
How Can AI Significantly Enhance ISO 27001 Security Controls and Compliance Efforts?
Artificial Intelligence (AI) technologies offer powerful capabilities to accelerate the implementation of security controls and improve the accuracy of audits by automating routine tasks and analysing vast datasets in real time.
What Are the Key Benefits of Leveraging AI in ISO 27001 Audits?
- Enhanced Efficiency: Automates the collection and validation of audit evidence, saving valuable time.
- Improved Accuracy: Utilises anomaly detection within system logs and configurations for more precise findings.
- Greater Scalability: Enables continuous monitoring across multiple systems and environments simultaneously.
How Can AI Streamline Evidence Collection and Monitoring Processes?
AI-powered tools can efficiently parse system logs, meticulously track patch levels, and verify policy enforcement without requiring manual intervention. Automated dashboards provide clear visibility into control deviations, trigger timely alerts for potential issues, and generate comprehensive compliance reports—freeing up your security teams to concentrate on critical remediation activities and strategic improvements.
What is Stratlane’s Distinct AI Advantage in Achieving ISO 27001 Certification?
Stratlane uniquely combines the expertise of seasoned auditors with proprietary AI algorithms to offer an accelerated and more efficient path to ISO 27001 certification. Our AI-enhanced platform intelligently correlates risk data across diverse environments, recommends optimal control sets tailored to your needs, and generates audit-ready evidence—all supported by the deep knowledge of our information security professionals.
What Are the Advantages and Challenges of ISO 27001 Certification for Small and Medium-sized Enterprises (SMEs)?
How Does ISO 27001 Certification Elevate Information Security and Build Trust?
Achieving ISO 27001 certification serves as a powerful testament to your organisation’s commitment to rigorous security practices, reassuring customers, partners, and regulatory bodies. It demonstrably reduces the financial impact of security incidents, significantly enhances your brand reputation, and unlocks new opportunities, particularly within regulated markets.
What Common Hurdles Do SMEs Typically Encounter in Achieving Compliance?
SMEs frequently face challenges related to limited budgets, a scarcity of specialised security expertise, and the need to balance security priorities with other pressing business demands. The inherent complexity of documentation and constraints on available resources can often delay implementation timelines. Effectively addressing these challenges requires strong executive sponsorship, a phased rollout strategy, and a pragmatic approach to tailoring controls.
How Can SMEs Best Prepare for the Upcoming 2027 Transition Deadline?
SMEs should proactively initiate their transition planning by updating relevant policies, conducting comprehensive staff retraining, and meticulously aligning their current controls with the updated 2022 framework. Conducting pilot audits is highly recommended to pinpoint any process gaps, and engaging experienced ISO 27001 partners early in the process can significantly streamline the transition journey.
How Does the ISO 27001 Certification Audit Process Typically Unfold in the UK and Europe?
The ISO 27001 certification audit process is structured into distinct phases: initial preparation, a two-stage audit, a formal certification decision, and ongoing surveillance activities.
What Are the Key Stages Involved in an ISO 27001 Certification Audit?
- Stage 1 Audit – Focuses on document review and assessing overall readiness for the main audit.
- Stage 2 Audit – Involves an in-depth, on-site evaluation of control implementation and effectiveness.
- Certification Decision – An independent certification body makes the final decision to issue the certificate.
- Surveillance Audits – Conducted annually to verify the continued maintenance and effectiveness of the ISMS.
These carefully structured phases ensure the maturity of your ISMS and its ongoing alignment with the requirements of the standard.
How Does Stratlane Conduct Its Advanced AI-Enhanced Audits?

Our AI-enhanced audits seamlessly integrate automated evidence gathering with invaluable human expertise. AI tools meticulously analyse system configurations and logs prior to on-site visits, allowing our auditors to concentrate on critical risk discussions and control validation—ultimately delivering faster, more insightful, and comprehensive assessments.
What Specific Documentation and Evidence Are Typically Required by Auditors?
Auditors will require access to key documents such as your organisation’s policies, Statement of Applicability (SoA), risk assessment reports, control implementation records, staff training logs, and incident reports. Utilising automated tools can significantly expedite the compilation of system logs, vulnerability scan results, and access review records, thereby accelerating the evidence submission process.
How Can You Effectively Maintain Your Certification After the Initial Audit?
Sustaining your ISO 27001 certification involves adhering to scheduled surveillance audits, promptly addressing any identified nonconformities, and committing to the continuous improvement of your ISMS. Regular reviews of performance metrics and up-to-date threat intelligence should inform your annual management reviews, ensuring the long-term integrity and effectiveness of your compliance posture.
Where Can You Access Essential Resources and Expert Support for ISO 27001 Compliance?
Accessing authoritative standards, insightful case studies, and professional services is crucial for organisations aiming to implement controls effectively and remain current with evolving best practices.
What Official Standards and Guidelines Should You Prioritise?
For the definitive ISO 27001 framework and detailed Annex A control definitions, always refer to the International Organization for Standardization (ISO). Additionally, national bodies such as the British Standards Institution (BSI) and the National Cyber Security Centre (NCSC) publish valuable complementary best-practice guidance.
How Can Industry Reports and Real-World Case Studies Provide Valuable Insights?
Industry analyses and practical case studies offer invaluable insights into real-world implementation strategies, highlight common pitfalls to avoid, and share crucial lessons learned. They provide practical guidance on effectively tailoring controls to suit diverse sectors and organisational scales.
Where Can You Find Reliable Training and Certification Services?
Organisations can engage specialised consultants for tailored workshops, comprehensive gap analysis, and expert readiness assessments for certification. To discover more about our structured audit methodology and advanced AI-driven approach, we invite you to explore our ISO 27001 Certification – Stratlane page.